A set of malicious packages impersonating Kraken, Solana and Monero has flooded NuGet’s server as hackers launch new scams.
NuGet, a manager used for packaging and distributing software written with the .NET framework, appears to be a target for bad actors seeking to exploit vulnerabilities, impersonating crypto-related packages.
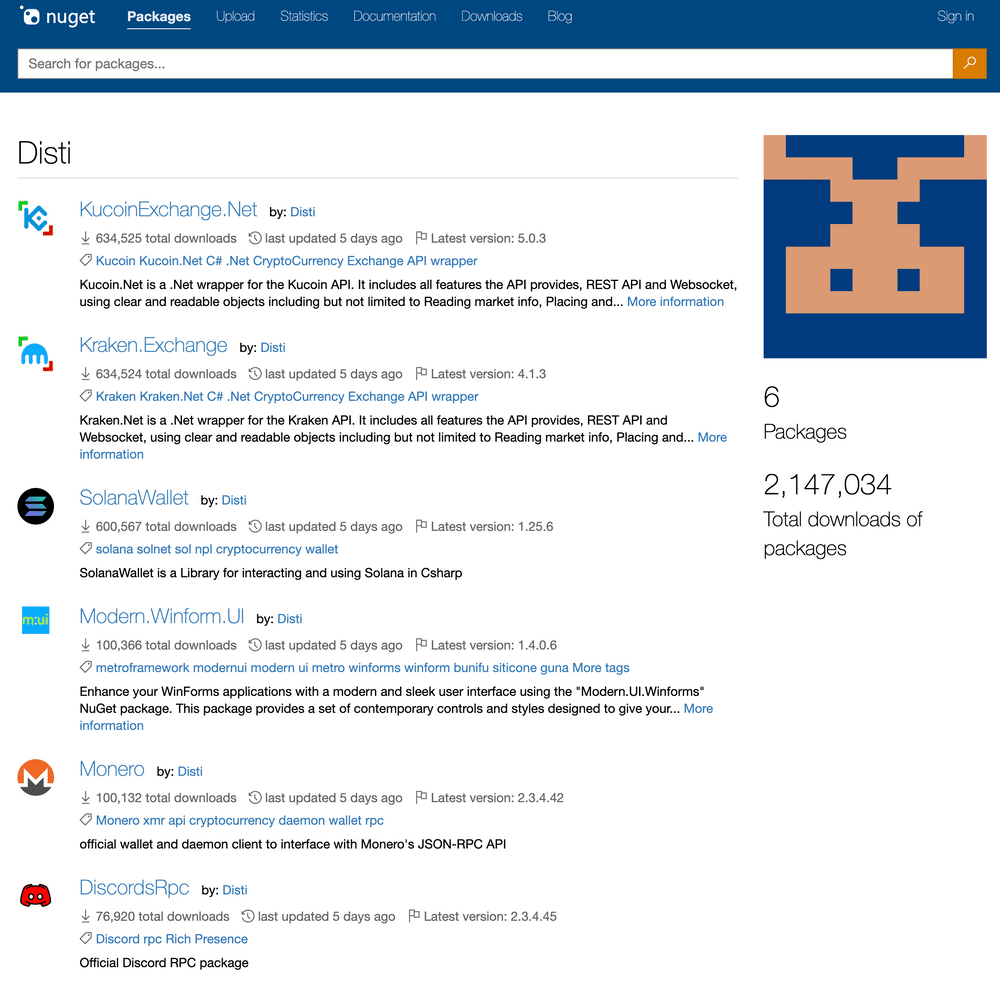
As first reported by Phylum researchers, six malicious packages — downloaded by a user named “Disti” — are pretending to be libraries and wrappers for Kraken, Solana, KuCoin and Monero. The bad actor reportedly also tried to bolster credibility by faking the download figures.
Once the malware is installed on a victim’s computer, it executes .cmd and .bat files with the help of two PowerShell scripts. Eventually, the scripts download an external file, trying to stay unnoticed by not producing visible output or errors.
After a long series of manipulations, the script downloads SeroXen RAT. This stealthy remote access trojan gained popularity when it was used alongside cheats for video games such as Call of Duty: Warzone and Fortnite. The trojan is well-known among cybercriminals as it gives them full access to a victim’s computer with low detection. As noted by BleepingComputer, the malware is still available on NuGet’s server.
As crypto.news earlier reported, a new iteration of the Ducktail phishing campaign also spreads PHP malware that can access and steal users’ Facebook accounts, browsing data, and even crypto wallets. The attackers are said to employ social engineering techniques and seek targets through LinkedIn, a professional networking website.
The malware is being distributed as an archive, including images, videos, and documents. Once the file has been downloaded and opened, browser cookies are read and transmitted to the hacker’s server.